Security
Rating
Solution
Menaya maps your cyber risks and anticipates their impact. This mapping assesses your cyber security maturity solely based on public information pertaining to the domain name of your organization.
The unparalleled Security Rating Solution developed by Menaya
Our Security Rating solution allows you to generate an automated vulnerability assessment and rating of the cyber risk level of your services.
Unlike other rating solutions, Menaya’s solution is in a class of its own. Its assessment based on 20 cyber-threat monitoring components allows you to accurately assess your organization’s cybersecurity posture.
Our Rating solution provides you with a rating of your potential exposure to ransomware, a type of cyber attack that can cause serious damage to your business. We also generate comprehensive and detailed compliance reports.
Our Security Rating solution caters to both the Management and IT departments. The solution generates strategic reports that present remedial actions plans and simple steps to remediate the vulnerabilities found.
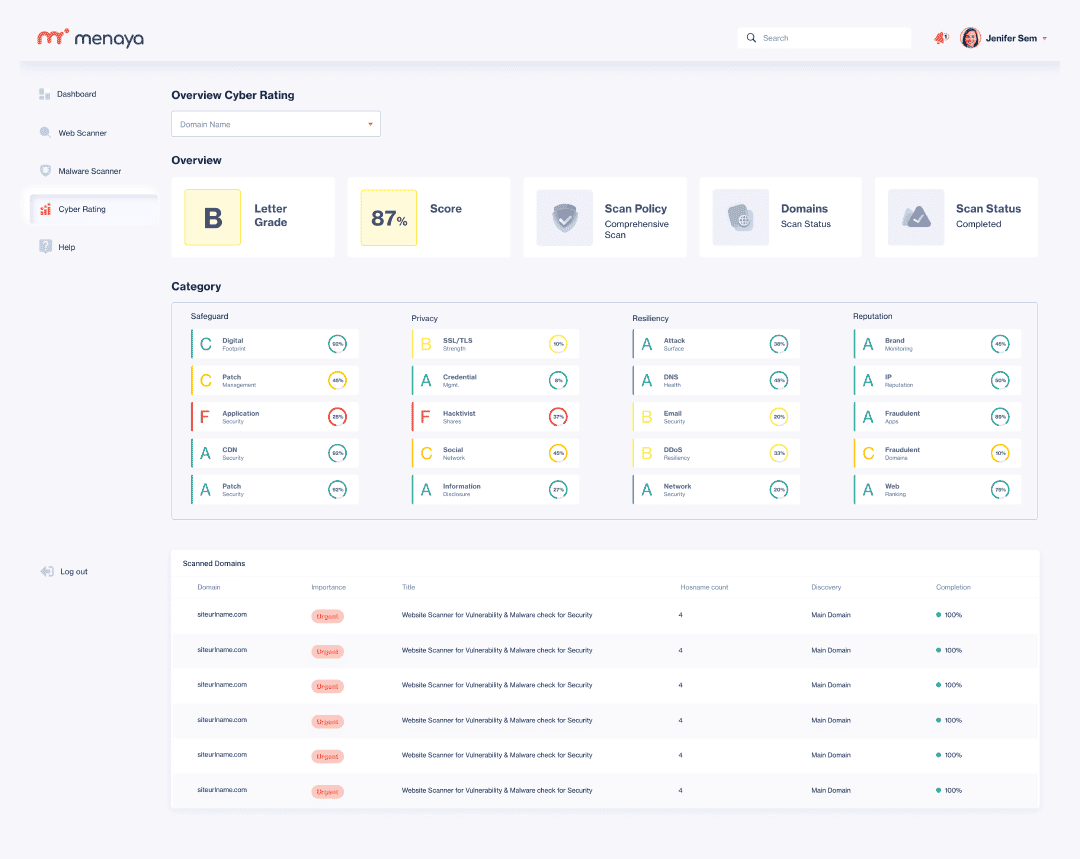
A 20-component risk map
Our system security assessment platform allows you to assess your organization’s cyber risk profile very quickly, while factoring in the different technical, financial and compliance considerations. The uniqueness of Menaya’s Security Rating solution comes from the 20 components that we review in detail:
Backup
Keep the software on your computers and network devices up to date to resist low-level cyber attacks. Hackers can exploit known technical vulnerabilities in operating systems and third-party applications when organizations are not quick enough to patch or update them.
Application security measures are designed to prevent data or application code from being stolen or misappropriated. Application security includes, but is not limited to, hardware, software, and procedures that identify or reduce vulnerabilities.
Businesses use content delivery networks (CDNs) - these are large systems of servers deployed in multiple data centers across the Internet - for online libraries like JQuery. Detect vulnerabilities in services such as edge caching, SSL offloading and edge routing.
Domains registered by scammers are used to launch phishing attacks, seeking to sell counterfeit products on spoofed sites or to use "typosquatting" domains to earn money off unintentional traffic from other sites.
Cisco, Alexa and Majestic track websites and rank them based on popularity, backlinks and referrals. This subcategory shows trends, page speed test results and Web Content Accessibility Guidelines (WCAG) 2.0 compliance results.
Confidentiality
A company's website is one of its main assets. As such, detecting any code or server vulnerability is crucial to a company's reputation.
The SSL/TLS protocol encrypts Internet traffic of all types and makes secure Internet communication (and e-commerce) possible.
When a website unintentionally reveals sensitive information to its users, depending on the context, some of it may get in the hands of a potential attacker. This can include usernames or financial information, for example.
Hacktivism is the act of hijacking a computer system or network for politically or socially motivated purposes. An example of hacktivism is a denial of service (DoS) attack that takes a system offline to prevent clients from accessing it.
Social media are part of a larger ecosystem of publicly accessible platforms expanding the attack surface for cybercriminals.
Resilience
Set of entry points on the border of a system, element of a system, or an environment in which an attacker can attempt to penetrate and extract data.
Your digital footprint is a collection of data that can be traced back to you. This includes IP addresses, domains, subdomains, email addresses, fingerprints and servers.
A DNS attack is a feat through which an attacker takes advantage of vulnerabilities in the Domain Name System (DNS).
An open technique for protecting email accounts, content and communications from unauthorized access, loss or compromise.
When a website unintentionally reveals sensitive information to its users, depending on the context, some of it may get in the hands of a potential attacker. This can include usernames or financial information, for example.
Reputation
Detecting malicious cyber attacks that hackers or cybercriminals use to make an online service or network resource unavailable to users.
Technical analysis of network failures, detection of critical ports, unprotected network devices, misconfigured firewalls and other service endpoints.
A business analysis process that monitors various web or media channels for information about the company, the brand and anything explicitly related to cyberspace.
Identifying IP addresses that send unwanted requests. Using the IP reputation list, you can identify if an IP address has a bad reputation or if it is a member of a botnet.
Fraudulent apps are used to hack/photograph employee or customer information. This category identifies fraudulent or pirated mobile/desktop apps on Google Play, App Store as well as pirate stores.
Backup
Keep the software on your computers and network devices up to date to resist low-level cyber attacks. Hackers can exploit known technical vulnerabilities in operating systems and third-party applications when organizations are not quick enough to patch or update them.
Application security measures are designed to prevent data or application code from being stolen or misappropriated. Application security includes, but is not limited to, hardware, software, and procedures that identify or reduce vulnerabilities.
Businesses use content delivery networks (CDNs) - these are large systems of servers deployed in multiple data centers across the Internet - for online libraries like JQuery. Detect vulnerabilities in services such as edge caching, SSL offloading and edge routing.
Domains registered by scammers are used to launch phishing attacks, seeking to sell counterfeit products on spoofed sites or to use "typosquatting" domains to earn money off unintentional traffic from other sites.
Cisco, Alexa and Majestic track websites and rank them based on popularity, backlinks and referrals. This subcategory shows trends, page speed test results and Web Content Accessibility Guidelines (WCAG) 2.0 compliance results.
Confidentiality
A company's website is one of its main assets. As such, detecting any code or server vulnerability is crucial to a company's reputation.
The SSL/TLS protocol encrypts Internet traffic of all types and makes secure Internet communication (and e-commerce) possible.
When a website unintentionally reveals sensitive information to its users, depending on the context, some of it may get in the hands of a potential attacker. This can include usernames or financial information, for example.
Hacktivism is the act of hijacking a computer system or network for politically or socially motivated purposes. An example of hacktivism is a denial of service (DoS) attack that takes a system offline to prevent clients from accessing it.
Social media are part of a larger ecosystem of publicly accessible platforms expanding the attack surface for cybercriminals.
Resilience
Set of entry points on the border of a system, element of a system, or an environment in which an attacker can attempt to penetrate and extract data.
Your digital footprint is a collection of data that can be traced back to you. This includes IP addresses, domains, subdomains, email addresses, fingerprints and servers.
A DNS attack is a feat through which an attacker takes advantage of vulnerabilities in the Domain Name System (DNS).
An open technique for protecting email accounts, content and communications from unauthorized access, loss or compromise.
When a website unintentionally reveals sensitive information to its users, depending on the context, some of it may get in the hands of a potential attacker. This can include usernames or financial information, for example.
Reputation
Detecting malicious cyber attacks that hackers or cybercriminals use to make an online service or network resource unavailable to users.
Technical analysis of network failures, detection of critical ports, unprotected network devices, misconfigured firewalls and other service endpoints.
A business analysis process that monitors various web or media channels for information about the company, the brand and anything explicitly related to cyberspace.
Identifying IP addresses that send unwanted requests. Using the IP reputation list, you can identify if an IP address has a bad reputation or if it is a member of a botnet.
Fraudulent apps are used to hack/photograph employee or customer information. This category identifies fraudulent or pirated mobile/desktop apps on Google Play, App Store as well as pirate stores.
Ransomware Risk Assessment
Thanks to its Cyber Security Rating solution, Menaya’s experts run uninterruptible monitoring schemes checking over 200 key ransomware risk indicators. It then automatically generates a ransomware sensitivity score and determines the probability of an attack.
We also provide full technical details on how to fix and remediate those assets that put your organization at risk. Together, we mature your cybersecurity program.

Ransomware Susceptibility Index
(RSI)
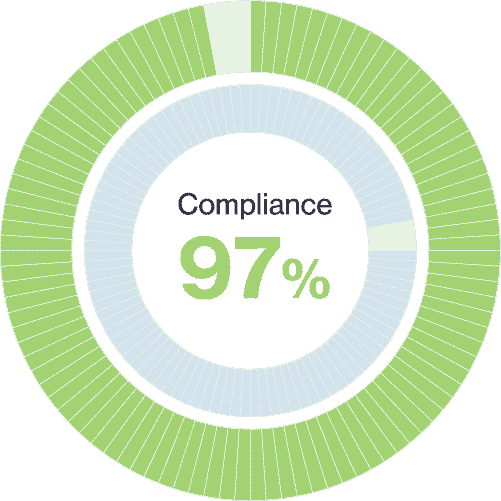
Compliance reports
After testing, our report correlates the cyber risk results with industry standards and best practices. The classification and scoring system allows you to measure any company’s compliance with various regulations and standards, including the following: NIST 800-53, ISO27001, PCI-DSS, HIPAA, GDPR, Shared Assessments, etc.
NIST 800-53

GDPR
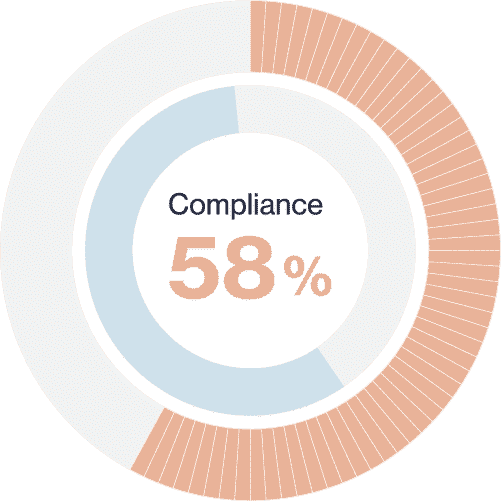
PCI-DSS
The benefits of Menaya’s Security Rating Solution
Quick and easy analysis of your business cyber risk profile
Our automated risk assessment and monitoring platform quickly assesses your company’s cybersecurity risk profile.
Financial quantification of your cyber risk
Menaya allows you to measure cyber risk in financial terms by putting cyber risk in clear business terms and maturing your cybersecurity program.
Hands-on recommendations to solve your organization’s weaknesses
We generate detailed reports that help you better understand your cyber risk exposure for strategic remediation decision-making.
Contact us to get your Cyber Security Risk Profile!
Contact us to get your Cyber Security Risk Profile!
Frequently asked questions
-
Is Menaya’s Security Rating Solution right for me?
With our cyber threat map, you will gain insight on how cyber criminals appreciate the cybersecurity-readiness of your organization as well as the risk level of your partners. Menaya's Security Rating solution is what you need if you want to reinforce your company's security. -
What does extrapolation of data mean?
Some information, when misinterpreted, can lead to an unreliable appreciation of risk. Indeed, some types of incidents are specific to a particular type of organization and therefore cannot be applied to all organizations - extrapolating data can lead to scoring errors. Menaya makes it a rule to refrain from any kind of data extrapolation throughout the entire assessment process, from mapping to scoring. -
Why turn to Menaya to secure my Website?
By choosing MenayaCysland and its Cyber Security Rating solution, you entrust us with the protection of your website so that you can focus on your business.
Solutions
Our solutions
Cyber Detection
Cyber Security Rating
Resources
Articles
FAQ
Glossary
Company
About us
Our offices
Media
MSSP Partners
Insurance partners
2022 © Menaya inc.
Company
About us
Our offices
Media
Resources
Articles
FAQ
Glossary
Partners
Become a partner
MSSP Partners
Insurance partners
2022 © Menaya inc.
2022 © Menaya inc.